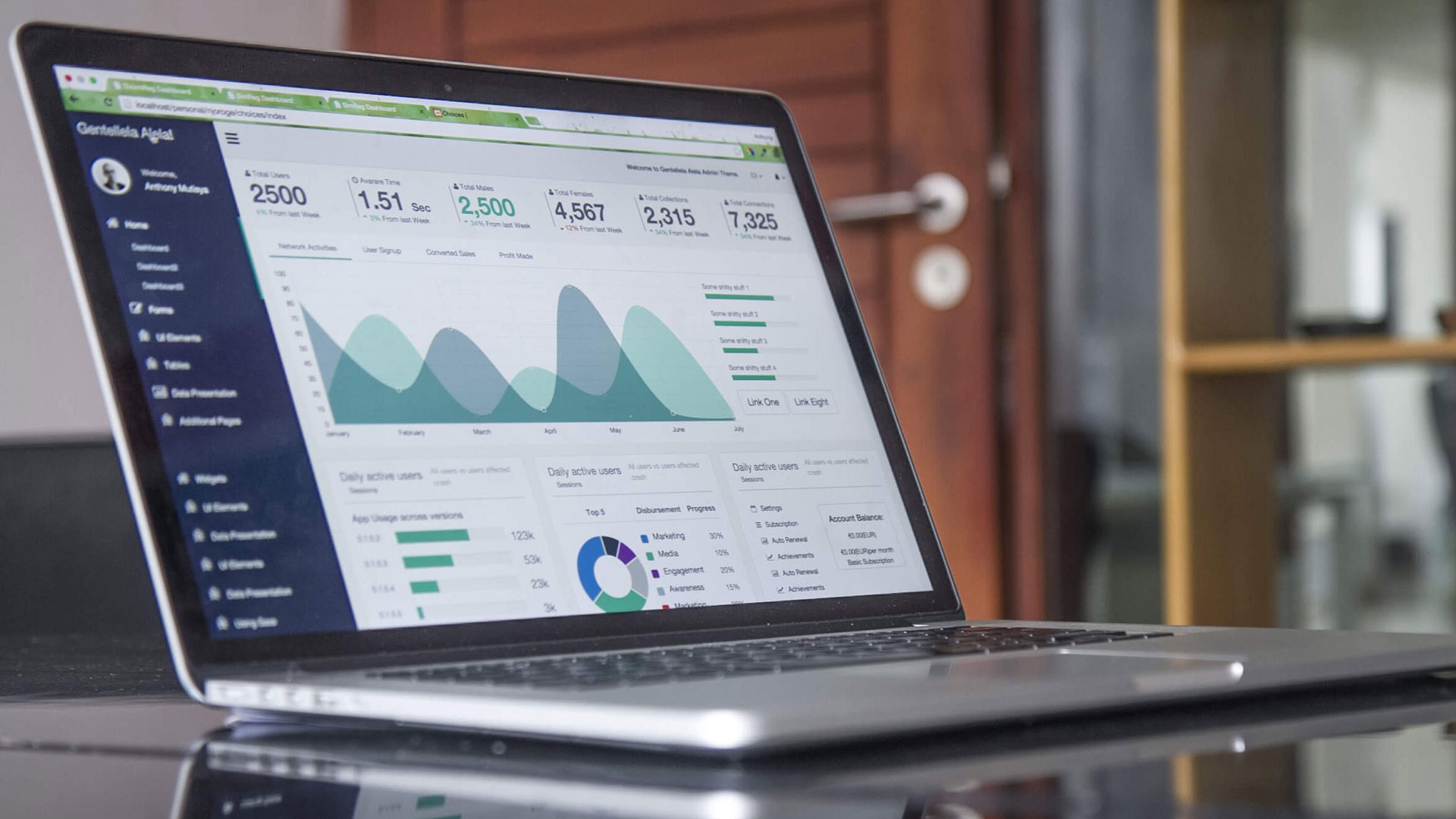
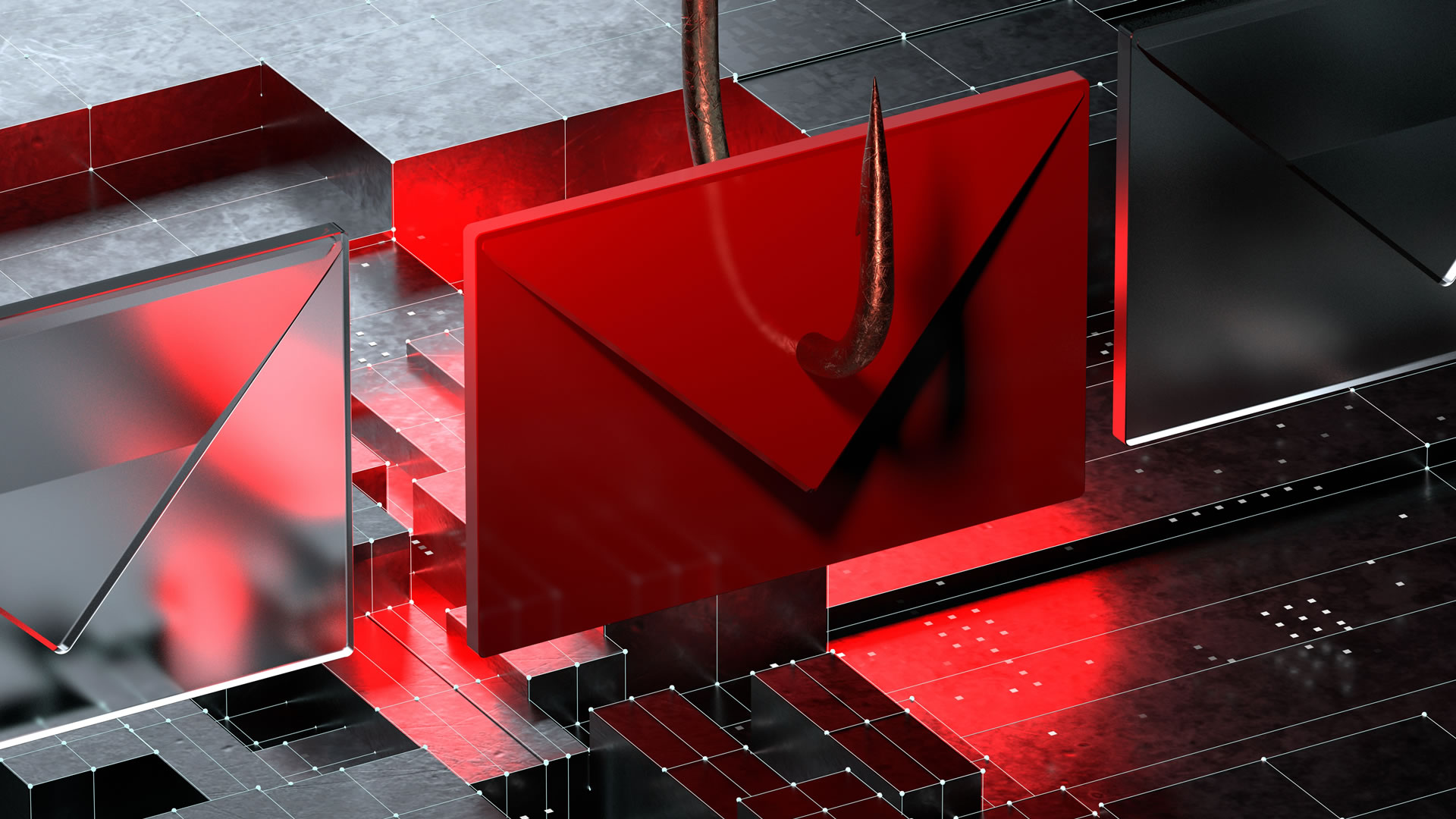
Email is the main way for them to exploit human error as criminals have a direct line to the vulnerable part of an organisation’s security. This being said, if a workforce isn’t aware of even the most basic email security best practices, how can you ensure a secure working environment? Let’s take a look at some of those best practices…
Utilise Blacklist and Whitelists
Let’s start with the obvious – a list for reliable, trusted domains, and a list for those not so trustworthy domains… Blacklists and whitelists are the best way for making sure your teams are only being contacted from the right domains.
Reduce spam with a good filter
A good spam filter is essential in all organisations. Not only for protecting against criminals, spam filters can really weed out distracting spam emails, although things will always slip through. Important note – impress on employees to never reply or click “unsubscribe” as this will confirm the legitimacy of their email address to the sender.
Gone phishin’
According to Barracuda, 93% of all cyber-attacks start with a phishing email, and better yet 97% of employees can’t reliable identify a phishing email. These are serious statistics. A phishing email is usually disguised as a familiar email e.g. a Pay Pal notification, to trick the victim into downloading a malware loaded ‘payload’ usually in the form of an attachment or link. Simulated phishing tests are proving popular in the IT world. Making sure your employees are clued up is the first line of defence against phishing attacks.
Performing malware scans
You can’t trash any email that looks unfamiliar. Then you’d likely be ditching legit items you want to see. Antivirus and anti-malware email security should be installed on top of a spam filter. This will scan all emails and attachments and alert an employee if there’s reason for concern.
Password Best Practice
Another easy win is creating strong, hard to guess passwords. I.e. abstract word and number combinations. Couple that with multi-factor authentication. This makes password logins require credentials on top of a username and password. Fingerprint scanning, facial recognition, security question etc.
Never use public WiFi for email access
Your typical WiFi hotspot is not run by an IT professional. Security is thus, lacking. Yes, boycotting public WiFi can be easier said than done. So, if 100% necessary, consider using encryption software.
In many ways, a business’s security is only as strong as its weakest employee. So, underpinning the above is sufficient education and training. This will make the first line of defence – humans – less prone to human error. Still, no strategy is fool proof. So, one final consideration is the frequent and automatic backup of all company data. This way, when threatened by a ransomware attack, a business can simply wipe and restore.